I am using Synology NAS to backup my Mac using Time Machine. After upgrade to MacOS Sierra (10.12.1) Time Machine backup sort of backed up my Mac. By sort of I mean it was showing Preparing backup... forever but if I entered Time Machine backup all backups even new ones were there.
To resolve the issue with "Preparing backup...":
To resolve the issue with "Preparing backup...":
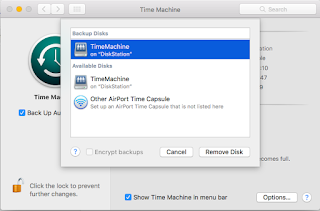 |
| Time Machine disk selection |
- I removed backup disk in Time Machine preferences
- Removed all Synology Diskstation passwords from KeyChain Access (not only Time Machine ones)
- Deselected Time Machine shared folder from Synology file services menu
- Disabled Mac file service (AFP) from Synology Control panel
- Dismounted all Synology mounted drives
- Enabled SMB 3.0 in Synology File services (Control panel)
- Enabled back Mac file service in Synology
- Selected Time Machine shared folder under Mac file services in Synology
- Opened Time Machine settings and Selected Time Machine disk from the list
- Selected Encrypt backup
- Entered username and password for Time Machine backup
- Entered password for encrypted backup
- Selected to Delete old backup (move .sparseBundle to other disk if you want to preserve it)
- Started backup

I followed this exactly and it sadly didn't work for me. My error is:
ReplyDeleteThe network backup disk could not be accessed because there was a problem with the network username or password. You may need to re-select the backup disk and enter the correct username and password.
Username and password are confirmed working via Finder. Any suggestions are appreciated.
It is crucial that you don't open/mount anything from Diskstation in Finder after you delete credentials in keychain. Time Machine should be the first instance asking you to enter username/password for Diskstation.
Delete